Application Scanning Guide
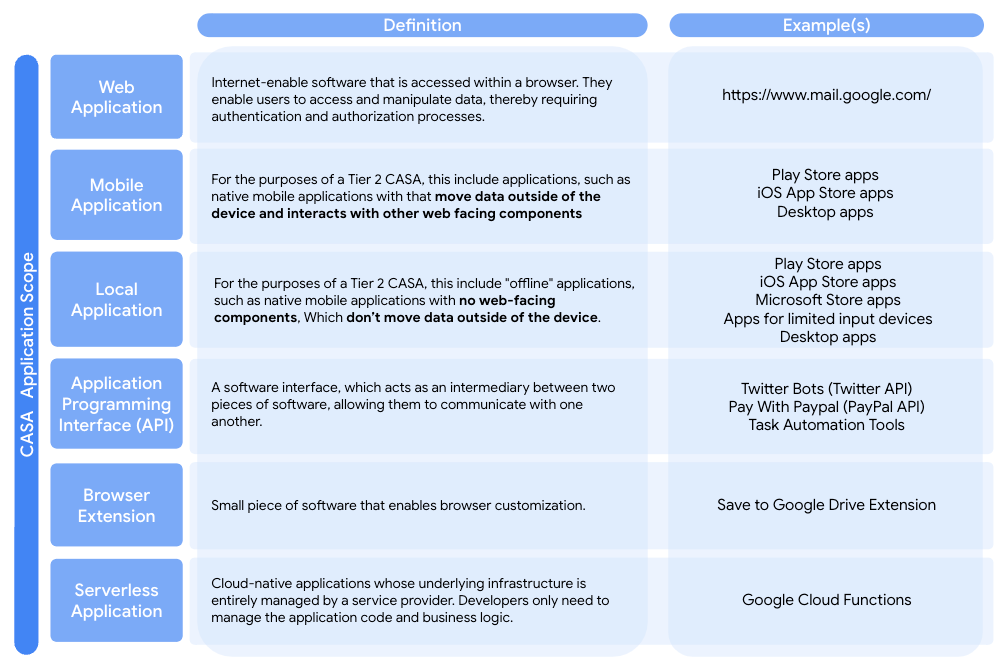
The purpose of this document is to provide the 3P developers with a step-by-step guide on how to execute a static or dynamic scan on your application. This document covers procedures of the two most commonly observed security evaluation tools Static Scanning and Dynamic Scanning. In each section, 3P developers may find steps to guide them through the process of how to configure automated scans. It is necessary for 3P developers to include the CWEs mapped to their submitted application type (web, mobile, API, serverless, local, or browser extension)
Once 3P developers complete the scans, the generated scan result (both CSV and XML) need to be uploaded to the portal. An assessor will review the submitted documents and provide the instructions for next steps. More information about the assessment process can be found here.
Scope
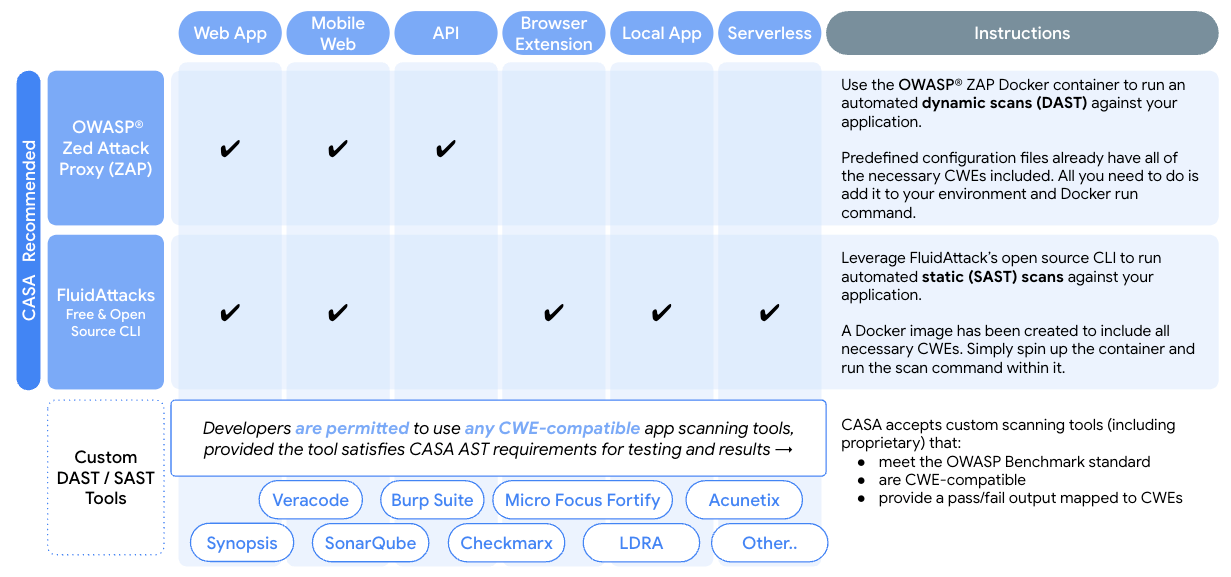
Developers are expected to scan their applications for a specific set of CWEs mapped to the OWASP Application Security Verification Standard (ASVS) v4.0. The number of applicable CWEs varies based on application type. All relevant CWEs have been included in the various configuration files provided for FluidAttack and ZAP. If these open-source tools are used for scanning, then developers only need to select the configuration file created for their application type. If another scanning tool is used, however, then developers must provide evidence that all of the relevant CWEs were included. This can be the configuration file or policy used by the scanning tool. Overall, developers need to provide the following:
If the recommended open-source scanning tools are used, developers must provide
-
Scan results of the FluidAttack or ZAP scan in CSV or XML format.
-
The policy or configuration file used to run the scan which shows all CWEs relevant for the application type.
-
Scan results in a PASS/ FAIL format, each mapped to a CWE. Scan results which only show FAILED requirements will also be accepted.
-
The “scorecard” results from running the DAST or SAST scanning tool against OWASP Benchmark.